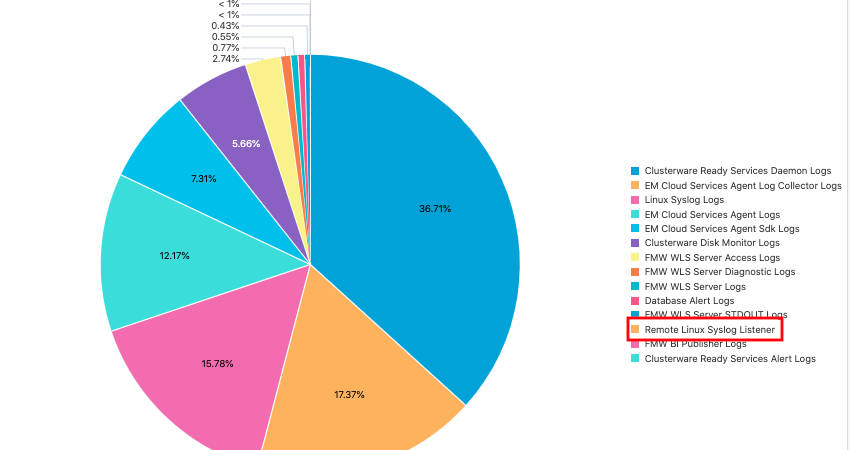
Sending logs to Oracle Management Cloud using Syslog Listener is part of a series of blogs designed to show the flexibility in options for uploading logs to Oracle Management Cloud Log Analytics. Be sure to read the rest of the blog series to see the other methods that can be used to send logs to Log Analytics.
Syslog Listener
Many applications and network devices allow you to configure logs to send to syslog. This can be accomplished by using something like rsyslog to allow a system to talk to another host and write to files, then the Cloud Agent can be configured to pick up those log files. This is the method we use to pick up the Oracle Exadata Storage Server logs. This type of method is well documented on the internet by different tools. For the Exadata setup, you can see the configuration whitepaper for steps.
The other option involves configuring the application or device to communicate directly over the network to a host/port combination where the Cloud Agent is configured to “listen”.
The first step for this is to install a Cloud Agent on a host where you want to receive log data from other applications/components. Validate that you have a free port you can use by checking with netstat -an|grep <port>.
Then in Log Analytics go to Log Admin > Log Sources and create a new Log Source. Provide a name and assign it a type of Syslog Listener. Select the Entity Type of Host and Parsers desired, for most cases the standard Syslog parser will work fine. For the Listener Patterns, you’ll enter the port which the application will communicate to the agent over, and the protocol (TCP or UDP).

Save this new log source, and click the “0” above Associated Entities to associate this to the host where you previously installed the Cloud Agent.

Click Add to select the Host entity.

Select the desired Host and click Select.
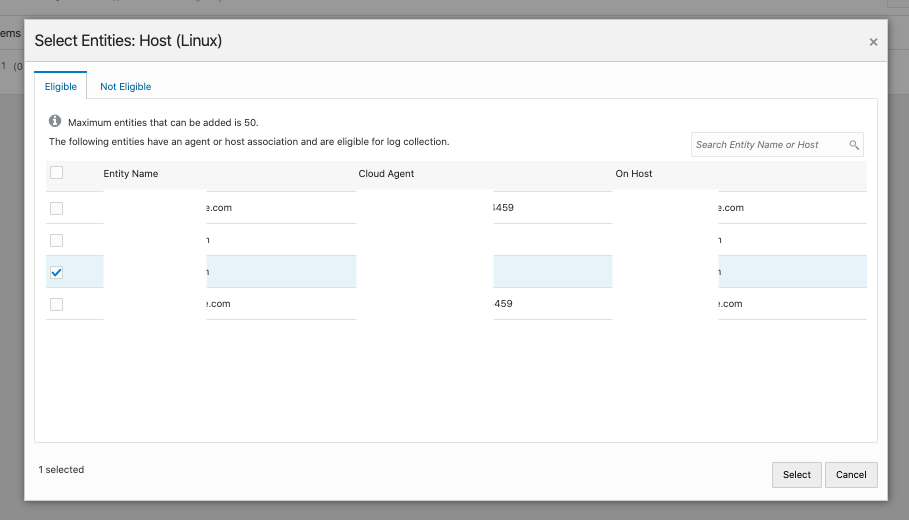
Confirm selection and click Save.

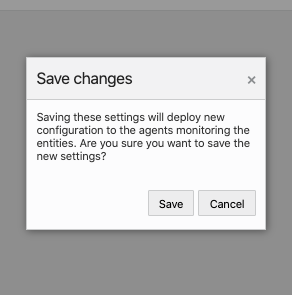
Click Save to confirm changes that will be sent to the Agent.
Now you will see that 1 entity has been associated to the Remote Linux Syslog Listener.

In my environment, I made a simple change to my rsyslog.conf environment to allow it to forward all logs to the host I associated my Log Source to, on the port I specified in the Log Source. This will enable the communication directly to the Cloud Agent. This is just a simple test, but if your network devices or applications allow log forwarding, you would follow the steps specific to them. I’ve seen this used by network devices and also Pivotal Cloud Foundry applications.
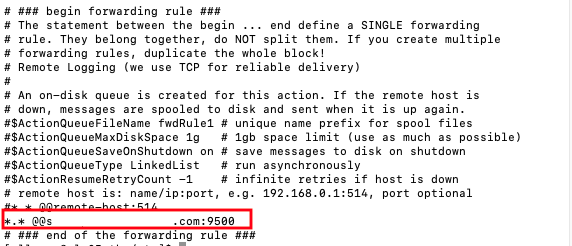
Before the changes will take effect, you. must restart rsyslog.

Now when I check my port usage on this host, I see that my port is being utilized.
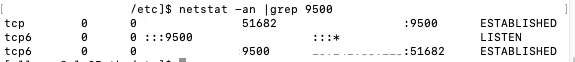
Shortly after, I also start to see my new Log Source listed in Log Analytics.
If I click on the Remote Linux Syslog Listener, I can see the log entries that have been collected since my restart of the rsyslog service.

For more details on the syslog setup, see the Log Analytics documentation.