In January, the DB Plug-in 12.1.0.7.0 was released for EM 12c. Not long after, my friend Brian found they added a new metric with default thresholds. The new metric group is Operating System Audit Files and the metric alerts on Size of Audit Files. Depending on the size and agent of your environment, you may immediately start getting notifications or pages as the default thresholds are 10MB/20MB, which can be quite small.
An example of the notification you might receive:
Host=xxxxxx.us.oracle.com Target type=Database Instance Target name=emrep Categories=Capacity Message=35.39 MB of Audit Trail files collected (.aud: 35.39, .xml: 0, .bin: 0) Severity=Critical Event reported time=Feb 6, 2015 6:53:56 AM PST Target Lifecycle Status=Production Operating System=Linux Platform=x86_64 Department=DBA Associated Incident Id=2103 Associated Incident Status=New Associated Incident Owner= Associated Incident Acknowledged By Owner=No Associated Incident Priority=None Associated Incident Escalation Level=0 Event Type=Metric Alert Event name=sizeOfOSAuditFiles:FILE_SIZE Metric Group=Operating System Audit Records Metric=Size of Audit Files Metric value=35.39 Key Value= Rule Name=DBA_Incident_Rule,Create incident for critical metric alerts Rule Owner=SYSMAN Update Details: 3.39 MB of Audit Trail files collected (.aud: 3.39, .xml: 0, .bin: 0) Incident created by rule (Name = DBA_Incident_Rule, Create incident for critical metric alerts; Owner = SYSMAN).
So if you’re planning to upgrade 1000 agents with the new Database Plugin, you might start getting a little nervous about receiving all of these pages. Since the metric didn’t exist before, it’s not included in your templates to be disabled. Even if it were in the templates, it would likely alert before you could reapply templates.
Luckily, Incident Rules provide a method to exclude a particular event when evaluating an Incident Rule.
From Setup -> Incidents -> Incident Rules, you’ll want to edit your defined Incident Rule. If you haven’t customized an Incident Rule, you can select the default Incident Ruleset and do a Create Like to clone and be able to edit.
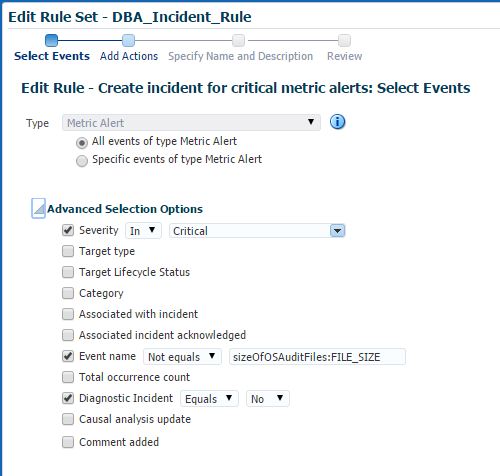
Select the Metric Alert rule, and click Edit.
On this first screen, you’ll see the Advanced Selection Options. If you expand this you’ll see an option for Event name. This is where you can exclude a specific metric event by select Not Equals and enter the event name. In the case of this metric, the event name is sizeOfOSAuditFiles:FILE_SIZE.
Click Next and Continue until you finally get to Save. To validate, you can use the Simulate Rules or trigger an alert to see if it sends the email.
This concept can be applied to help filter out other events, or categories of metrics as needed.